Week 8.1-3: Networking I Class Notes, Activities, and Follow-Up
#networking #UofTBootcamp #classwork #dns #binary #OSI #wireshark
Follow-UpQuestions
Layer 2: data link
From class slides:
– class covers arp here which yes, tracks MAC so layer 2 but isn't ARP itself a layer 3 (network) protocol?
– what does “primary vendor for the MAC addresses” mean? in Activity 8.3.1 on ARP packets
– do we need to know the details of TTL columns?
– STILL CONFUSED ABOUT LAYER 1-2!!!!!
Layer 3: network
Layer 4: transport
– asynchronous response > does this count as one request/response cycle?
From class TCP demo:
– Where is the flag set to 1 or 0 in the tcp packets for Wireshark?
Layer 7: application
From homework:
– authoritative vs non-authoritative DNS & usage/security implications?
– DNS vulnerabilities question: why was hacker able to access server as root to create ARP spoof and is there evidence of this?
NOTES ON TROUBLE-SHOOTING FROM MIRZA @ END
Subnetting Basics
- flat networking = everyone on the same network
- the use of subnetting to create segmentation bc otherwise it becomes congested – router in between networks, switch within a network
subnetting also called “broadcast domains”
as soon as you fire up a machine, it starts broadcasting
Layer 2: Data Link
enumeration: the process of gathering data for a specific network, usually for the purpose of finding new ways to gain access into that network
ARP: Address resolution protocol: find the MAC address of a device from an IP address
- communication between devices on a local network
- example: ethernet network that requires physical addresses to be known before sending packets
ARP request and reply process:
(1) device sends ARP request message containing the IP address of the receiving device
(2) all devices on a local network segment see the message but only the device that has the IP address response with ARP reply containing its MAC address
ARP cache:
– mapping of MAC address to IP address that is added to the ARP cache — called dynamic ARP entry of the
– ARP cache timeout: record is removed from ARP cache so any future requests for hosts require a new ARP request
Wireshark + ARP:
arp.code == 1 shows only ARP requests
arp.code == 2 shows only the ARP responses
SECURITY IMPLICATIONS of ARP:
ARP cache poisoning or ARP spoofing
– terms used interchangeable though poisoning is corrupting and spoofy is impersonation
– Any device on the network can answer an ARP request regardless of whether the original message was intended for it or not. F
– example: If Computer A asks for the MAC address of Computer B, an attacker at Computer C can respond and Computer A would accept this response as authentic.
DETECT ARP ATTACK:
arp -a will check your current mapping
Boot Camp Example:
The good host's address is <example ip> and the good host's correct MAC address is <example MAC address>
– the hacker will send a spoof ARP message so that all future traffic intended for the good MAC address will instead to the hacker's MAC address. It will look like this when detected with WireShark:
Duplicate IP address detected for 192.168.47.2 (00:0c:29:1d:b3:b1) - also in use by 00:50:56:fd:2f:16 (frame 301)
ARP Poisoning Attack Steps According to Self-Study:
1. Attacker Selects a Victim Machine/Machines:
– select a target such as a specific endpoint, a group of endpoints, or a network device like a router.
– routers are attractive targets because a successful ARP poisoning attack against a router can disrupt traffic for an entire subnet
- Attacker Launches Tools and Begins the Attack:
arpspoof or driftnet
Attacker does something with the steered traffic:
inpsect, alter, blackhole it, etc.
TWO general types of ARP Poisoning Attacks
1. wait to see ARP requests for a particular target and issue a response
2. send out an unsolicited broadcast message known as a gratuitous ARP
Man-in-the-Middle (MiTN) Attack:
– attacker sends out falsified ARP responses for a given IP, typically the default gateway for a subnet
– victim machines populate their ARP cache with the MAC of attacker's machine instead of local router's MAC address
– Victim machines now forward network traffic to the attacker
– tools like Ettercap allow attacker to act as proxy for viewing or modifying info before sending to intended destination
– victim will never notice
Denial of Service (DOS) Attack:
– denying one or more victims access to network resources
– attacker sends out ARP Response messages that falsely map hundreds or even thousands of IP addresses to a single MAC address, potentially overwhelming the target machine
– type of attack, such as ARP flooding, can also be used to target switches, impacting performance of entire network
Session Hijacking
– similar to MiTM except attacker does not directly forward traffic from victim machine to intended destination but instead captures a genuine TCP sequence number or web cookie from the victim to use it to assume the victim's identity
– can be used to login anywhere!!!
Consequences of ARP poisoning attack?
- ARP caches are deleted in anywhere from a few minutes to several hours so no permanent infection
- can be chained in larger campaign
MITIGATION:
(1) Static ARP Tables:
– highly effective but huge admin burden bc changes require manual updates of ARP tables across all hosts, making static ARP tables unfeasible for most larger orgs
– can carve out separate network segment for static ARP tables where sec is crucial
(2) Switch Security:
– Business-grade ethernet switches have __Dynamic ARP Inspection (DAI) used to eval validity of ARP messages, drop suspicious/malicious. Config rate of ARP messages to prevent DOS.
(3) Physical Security:
– ARP messages are not routed beyond the boundaries of the local network so would-be attackers must be in physical proximity to vitim network or already have control of a machine on network
(4) Network isolation:
– ARP messages don't travel beyond local subnet. therefore, well-segmented network will be less susceptible to ARP cache poisoning
(5) Encryption:
– mitigate potential damage, i.e. SSL/TLS encryption on web makes MiTM attacks to capture login credentials a lot harder.
—-Who has 192.168.47.1? Tell 192.168.47.171
ESP: Encapsulating Security Payload (ESP) protocol:
– provides data confidentiality, and also optionally provides data origin authentication, data integrity checking, and replay protection.
ESP vs Authentication Header (AH) protocol is that ESP provides encryption, while both protocols provide authentication, integrity checking, and replay protection. With ESP, both communicating systems use a shared key for encrypting and decrypting the data they exchange.
Layer 3
ICMP: Internet Control Message Protocol echo request = ping
- a protocl that network devices use to send error messages and operational info about whether a requested service or host can be reached
- not usually used to exchange data
- devices can block this
traceroute: like ping but with time taken to travel across each hop from source to destination
TTL: Time to Live: Prevents data from being stuck in infinite loop
- how long a data packet can exist in a network
- decrementing hop counter – every router that forwards the packet decrements (reduces) the
TTLvalue by one - once
TTLhits zero, will send a “time exceeded” error - different OS have different default TTL so an easy way to figure out what server you are working with if pentesting is to
pingand check that:
https://ostechnix.com/identify-operating-system-ttl-ping/
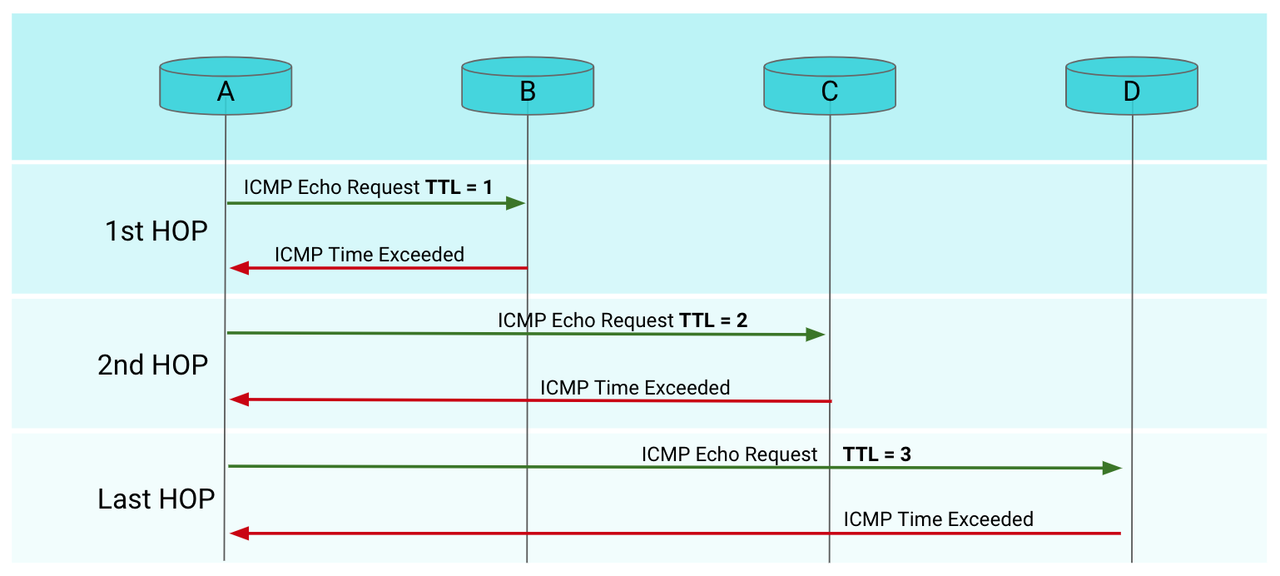
***means time out
Layer 4: TCP
TCP: Connection-Oriented Protocol
- used for:
HTTP/S,FTP,SSH,SMTP
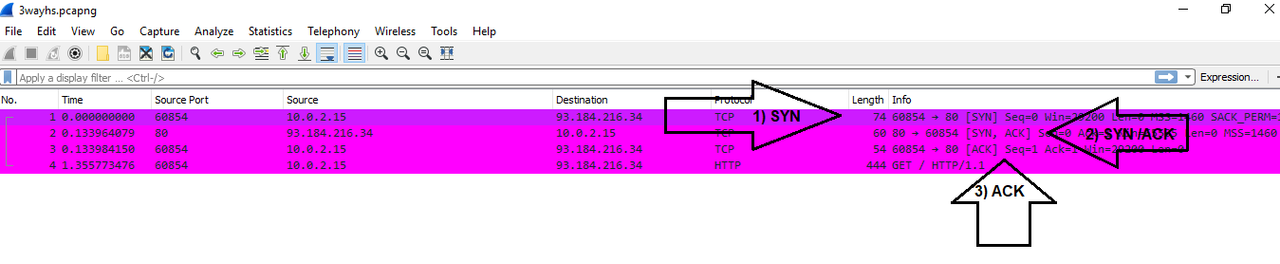
The Three-Way-Handshake
(1) **SYN** (Synchronize) – client to server
– client sends SYN data packet to the server to determine if it is ready to open a connection
(2) **SYN/ACK** (Synchronize/Acknowledge) – server to client
– sever acknowledges or confirms receipt of the SYN packet
(3) **ACK** (Acknowledge) – client to server
– client acknowledges receipt of the SYN/ACK packet
Four-Way Termination
(1) **FIN** (Finish) – client to server
– client sends a FIN packet to server to close the connection
(2) **ACK** (Acknowledge) – server to client
– server acknowledges receipt of FIN packet
(3) **FIN** (Finish) – server to client
– server terminates connection, sends a FIN
(4) **ACK** (Acknowledge) – client to server
– client acknowledges the termiantion
UDP: Connectionless
- reducing latency versus transmitting all data
- used for
pingandtracerouteorVoIP
WIRESHARK: Syn Packets
tcp.flags.syn ==1 && tcp.flags.ack == 0 to view only SYN
tcp.flags.syn ==1 && tcp.flags.ack == 1 to view only SYN/ACK requests
tcp.flags.syn == 0 && tcp.flags.ack == 1 to view only ACK
tcp.flags.fin == 1 to view FIN flag set to 1
WIRESHARK + PORTS
- “The important takeaway is that in this SYN scan, the behavior of a closed port is one packet in a conversation.” ???
Wireshark Open Port Behaviour:
– how to look for an open port? An open for TCP would be one where the initial synchronization step of the 3 step handshake has been acknowledged so your filter is: tcp.flags.syn == 1 && tcp.flags.ack == 1
– behaviour of open TCP port is as expected: 3 packets in a conversation:
 ]
]
– TAKEAWAY: OPEN TCP = 3 PACKETS
Wireshark Filtered Port Behaviour:
– A filter port indicates that a firewall, filter, or other network issue is blocking the port
– can be created by a server or network firewall, router, or security device
– servers typically do not respond to filtered ports
– TAKEAWAY: FILTERED = 1 PACKET
Wireshark Closed Port Behaviour:
– for closed ports, server's firewall will often respond with RST flag to indicate that they are not accepting connections.
– configurable in firewall's settings
– TAKEAWAY: CLOSED = 2 PACKETS
Wireshark View STATES of all ports:
- Statistics —> Conversations
Security Implications
- use firewall to block source IP of suspicious activity
Syn Analysis Activity:
3 ports have 5 packets: 53, 80, and 22
– Following port 53 shows that there was an initial request from 36050 to 53, a response back, and then 3 x TCP Retransmissions from 53 to 36050 meaning that “the TCP sender is not seeing ACKs that cover earlier transmitted packets in a timely manner.”
– same with other ports
Week 8.1
- A hacker logged into Microsoft Outlook with the stolen username and password of Acme's CFO. The hacker sent an email to the head of accounting asking them to wire $10,000 to a foreign account owned by the hacker.
- logging in means sending a request for a session
- sending an email in TCP/IP terms means:
(1) APPLICATION LAYER: write email in email client > message data is sent to a a port for the relevant service, likely 25 for SMTP?
(2) TRANSPORT LAYER: encapsulates the data with TCP or UDP header with destination and source ports —–> segment is sent to...
(3) NETWORK LAYER: encapsulates the segment inside IP packet with source and destination IP —–> packet is sent to...
(4) LINK LAYER: packet reaches physical hardware, encapsulates into frame with source and destination MAC addresses —–> frame is received by the link layer on the other end.
- the receiver of the email has to make a request to the email server to retrieve the email before they can read it. the retrieved email is the response.
- A hacker used Firefox to visit the administrative website of Acme Corp, where they attempted to log into the CFO's account multiple times, until they correctly guessed the password.
visiting the website:
(1) DNS look-up so that the URL can be translated into the IP address of the server containing the resources for the site. Checking
– browser cache
– OS system cache
– Router cache
– ISP DNS cache
(2) browser sends an http request to the server
(3) server responds
(4) browser renders server's response
(5) this can be synchronous or asychronous
- each time the hacker tries to log into the account, a session request is made to the server from browser
- A hacker stole the Acme CFO's mobile phone. Login credentials were saved on the phone, allowing the hacker to log into Acme Corp's mobile admin application.
- same idea?
—
Design the office with the following computer and network devices:
- (6) Employee computers
- (2) Switches
- (1) Router
- (2) Load balancers
- (1) Firewall
- (1) Representation of the internet
- (1) Server
- (1) Wireless access point with (1) firewall to protect it
DMZ
add the server and load balancers to the DMZ
- internet || firewall || router –> everything else?
- load balancer between server and client
- DMZ switch between firewall and public-access servers?
—
Convert the following binary representations into numeric IP addresses:
11000000101010000100010110010001> 192.168.69.145 (private)00001010000000000000000000101010> 10.0.0.42 (public?)11000000101011000100010110010001> 192.172.69.145 (private)00101001001011011011011000100000> 41.45.182.32 (public?)00001010000000000000000001001100> 10.0.0.76 (public?)
Compare the numeric IP addresses to the Acme server list and determine which server the IPs belong to.
Summarize your findings to determine what resources the hacker is trying to access.
Your security manager also found the following binary data in the hacker's logs:
100010001111011111000111011001010001101000110110
Determine what this binary data represents.
spoofing a DNS on linux
/etc/hosts is where the DNS translation occurs on Linux
The syntax for adding a DNS look up is: [ip] [domain]
For example: 137.74.187.102 krebsonsecurity.com
– only works on root though
Week 8.2
Translating raw binary into readable format
Log file 1
GET / HTTP/1.1
Host: widgets.com
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/66.0.3359.117 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,nb;q=0.8
Log file 2
File Transfer Protocol (FTP)
230 Login successful.\r\n
Response code: User logged in, proceed (230)
Response arg: Login successful.
Log file 3
TLSv1.2 Record Layer: Application Data Protocol: http-over-tls
Content Type: Application Data (23)
Version: TLS 1.2 (0x0303)
Length: 56
Encrypted Application Data: d03ff41452da9e9c3ec76cbeb35e8ffc1f64bf80f512924a?
Log file 4
Domain Name System (query)
Transaction ID: 0x18b6
Flags: 0x0100 Standard query
0... .... .... .... = Response: Message is a query
.000 0... .... .... = Opcode: Standard query (0)
.... ..0. .... .... = Truncated: Message is not truncated
.... ...1 .... .... = Recursion desired: Do query recursively
.... .... .0.. .... = Z: reserved (0)
.... .... ...0 .... = Non-authenticated data: Unacceptable
Questions: 1
Answer RRs: 0
Authority RRs: 0
Additional RRs: 0
Queries
applegate.com: type A, class IN
[Response In: 623]
Log file 5
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: Technico_65:1a:36 (88:f7:c7:65:1a:36)
Sender IP address: 10.0.0.1
Target MAC address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Target IP address: 10.0.0.6
Log file 6
HCI H4
[Direction: Unspecified (0xffffffff)]
HCI Packet Type: HCI Command (0x01)
HCI Command – Read Local Supported Features
Command Opcode: Read Local Supported Features (0x1003)
Parameter Total Length: 0
[Response in frame: 4]
[Command-Response Delta: 4.181ms]`
Determining source and destination ports, protocol, and summarize findings for each request in logfile:
Log file 1
Source: 192.168.1.9:50152
Destination: 192.124.249.168:80
Protocol: TCP 6
Summary: stealing of accessing data?
Log file 2
Source: 10.0.0.42:53367
Destination: 35.186.241.40:443
Protocol: TCP 6
Third one is also TCP. So exciting. I'm enthralled.
OSI Modeling
LINK: https://write.as/effyverse/networking-basics-47md
Review the list of 10 suspicious activities and determine which of the seven OSI layers each falls under:
1) A networking cable was cut in the Data Center and now no traffic can go out. Layer 1: Physical
2) A code injection was submitted from an administrative website, and it's possible that an attacker can now see unauthorized directories from your Linux server. Layer 7 Application for the code inject and layer 3 for the server?
3) The MAC address of one of your network interface cards has been spoofed and is preventing some traffic from reaching its destination.
Layer 2: data link
4) Your encrypted web traffic is now using a weak encryption cipher and the web traffic is now vulnerable to decryption.
Layer 6: Presentation
5) The destination IP address has been modified and traffic is being routed to an unauthorized location.
Layer 3: Network
6) A flood of TCP requests is causing performance issues. Layer 4: Transport
7) A SQL injection attack has been detected by the SOC. This SQL injection may have deleted several database tables. Layer 5: Session
8) A switch suddenly stopped working and local machines aren't receiving any traffic. Layer 2: Datalink
9) An ethernet cable was disconnected and the machine connected isn't able to receive any external traffic. Layer 1: Physical
10) Traffic within the network is now being directed from the switch to a suspicious device. Layer 3: Network
HOW TO APPLY THE OSI TO TROUBLE-SHOOT?
Question: How would one trouble-shooting an unreachable IP given only the information available from ping?
THE GOAL: is to narrow down your problem domain methodically
- server admin/team –> check ilo connection (console connection) to narrow down network vs server problem, if connected, validates that server is good. if not, check server itself
layer 1-2
– check hardware: beyond server, check switch
– enterprise switches are smart
– if you know the NIC, you can find the ARP translation to trace the MAC address
– once you have the MAC, you check its switch: from the switch perspective, are you seeing the server? if yes, you have validated that physical layer is good
– if layer two is good, you should be able to find the mac address
layer 3
– layer 3: is this an IP problem or does it affect all the servers on this subnet?
– if you can ping the other IPs, recheck the hardware because every other IP is working so it's a problem with localhost not network aka it is the specific machine pinging from and not necessarily the machine we are pinging to
– reverse the ping direction to check
– VLAN
– opnet/tcp dump – track the packet