Week 9.1: Lectures Notes, Class Activities on Routing, DHCP, NAT, 802.11
#networking #dhcp #nat #bridgemode #tcpip #OSI #mask #subnet #gateway # definitions #wireshark #aircrackng #80211
Follow-Up Questions
- the Wireless Toolbar no longer exists in view > it is now in Wireshark > Preferences > Protocols > IEEE 802.11
- DHCP attack bonus question
- Analyzing Wireless Security activity follow-up on beacon = WAP?
- Final activity: no WPA version = no security? + meaning of all the
802.11info terms
Self-Learning Notes
DHCP is an extension of BOOTP mechanism: DHCP uses BOOTP as its transport protocol
Activity 9.04 on DHCP Attacks
These employees are receiving error messages saying no local IP addresses are available, indicating a potential issue with DHCP:
- no local IP addresses available = likely a starvation attack
- Create a filter to determine the count for each DHCP activity:
- DHCP Discover:
dhcp.option.dhcp == 1– @150 - DHCP Offer:
dhcp.option.dhcp == 2–@32 - DHCP Request:
dhcp.option.dhcp == 3@1
- DHCP Discover:
QUESTION: Why does the Request say *REF*?
- Based on these results, summarize what type of attack may have occurred, and why you believe Acme Corp's employees are having network issues.
- there were 150
DHCP Discoverrequests and 32DHCP Offerresponses so it is likely that most of these requests were fraudulent and made the DHCP server run out of IPs.
Bonus
- Analyze the source MAC addresses of the DHCP activities and summarize what the attacker is doing.
QUESTION: What does this mean?
[Expert Info (Warning/Protocol): Source MAC must not be a group address: IEEE 802.3-2002, Section 3.2.3(b)]
Activity: Analyzing Wireless Security
- all the beacons are wireless routers, yes? 45
- 44 using WPA1, 1 using nothing?
Aircrack-ng Practice Activity:
KEY FOUND! [ 1F:1F:1F:1F:1F ]
– ARP flood attack clearly happening
– 802.11 has a lot of: Acknowledgement, Association Response, Authentication, Clear-to-Send, Disassociate
– 1 x 802.11 Beacon frame from SSID Appart,BSS Id: Arcadyan_12:32:29 (00:12:bf:12:32:29), with no security???
- There areIGMPv2` packets: IGMP (Internet Group Management Protocol) is a Host-Router Multicast Signalling Protocol that provides dynamically registration of the hosts to the desired Multicast Groups.
9.1 CLASS NOTES:
NAT Pathway:
(1) connecting to internet:
– outbound packet's destination port is standard, i.e. 80 or 443
– source port is randomly generated and unique for each connection
– when website replies, it sends packets back to you with source/destination IPs reversed
In detail: Loading Reddit:
– client sends packet to router to Reddit's IP + port 80/443 with source data of aka TRANSPORT LAYER encapuslates this data
– computer checks its subnet mask adn compares its own IP and the destination IP for computer to determine if a destination is beyond teh same router or if it'll need routing services: ARP Resolution Request
Example:
[192.168.0.2] [255.255.255.255] [ Who has router IP 192.168.0.1? ] Broadcasted on LAN
[192.168.0.1] [192.169.0.2] [ I have the Router IP, and you can reach me via MAC Address ffff ]
Your computer now knows how to reach the router, so now it fires the porn browsing packet to the router:
[192.168.0.2] [1.2.3.4] [ open connection ]
The router, upon receiving this packet, is smart enough to know that it's a connection request, so first it adds the source, destination and port to something called a NAT table, which looks like this:
Source Port Destination Port Local IP Remote IP
96354 80 192.168.0.2 1.2.3.4
88965 22 192.168.0.3 4.5.6.7
12345 8888 192.168.0.99 9.9.3.9
- router then forwards packet out to internet, changing source IP from to its own unique IP
can also change source port in order to avoid conflict since multiple machines could be attempting to reach reddit.com at same time and could be using the same source port numbers
NAT: is the table that the router keeps that maps the original internal ip/port to the translated ip/port number that the router changed the packet to
when reddit replies, router looks up received destination port numbers (the destination IP will always be the router's IP)
translation destination of incoming packets to original IP/port
since
TCPhas an explicit connection handshake/termination process, router is able to see when connections are terminated adn clear those from tableUDPis trickier because it's “stateless” so the router basically has use a timeout that resets every time a new packet is seen.
PUBLIC IP & NAT:
Every device on the internet has an IP address. This address must be unique, there can be no two devices with the same IP. The number of IP addresses is limited, and mostly used up. There is a group of addresses that have been reserved for use only in internal networks. This works because the devices sharing an address cannot see each other – they are on different networks with no route between them.
Nat is implemented by a device (a computer, a router, or a firewall) that has two network connections, one to the internal network, one to the internet. When a device on the internal network wants to connect outside, it sends its messages (packets) to the NAT device. The NAT device strips the address of the original device and substitutes its own, then sends it out to the internet.
When the reply comes back, the NAT device then strips its own address, substitutes the address of the original device, and sends it to the internal network.
In this way, many devices can share one IP address.
LAN: local area network
- will have: a network address (unusable), a mask (how mnay IP addresses are usable minus the network and broadcast, and a broadcast address (unusable)
- default gateway/default route is usually network+1 or broadcast+1
Gateway:
- in networking: the “default-gateway” on a single egress-point network (which is typically how a lot of networks are put together)
- but “gateway address” or “gateway device” or “gateway” can mean different things
- traffic needing to go from private to public networks and public to private networks or even private to private needs to go through gateway
Mask: defines how many IP addresses are usable minu the network and broadcast addrsses
- how a device (computer, router, etc) determines if a destination IP is local to an interface or not.
NAT: Network Address Translation (PUBLIC IP)
- “Speaking of IP, there aren't enough to go around so let me take that 1 public address your ISP gave you and “split it up” into many private ones for your devices”
- router maintains address book where it maps all your devices internally
- useful in IPV4 because you only get 1 external IP so to the outside world, your devices all appear to come from just 1 source
- 1-to-many relationship like a company where there are many employees but you only see the company name
DHCP: Dynamic Host Configuration Protocol (PRIVATE IP)
- “You don't have to manually assign IP addresses to your devices, let me do it fo r you”
- probably running on router at home
- will ask
DHCPserver “hey can I get an IP”,DHCPsays “ok, let me check for one not currently used to give to you” —> automates process of assigning IP yourself - often run by default with
NATbut it's not a requirement, can turn it off but will have to do IP assignments and avoid collision yourself
- DHCP is a Layer 7: Application layer protocol, that uses two UDP ports:
- Port
67is used by the server - Port
68is used by the client.
Bridge Mode
- whatever device you have in a middleman who doesn't care about the traffic rule; it only hands things from one end to the other
DHCP (Dynamic Host Configuration Protocol)
Four-Step Process
- DHCP Discover: find the DHCP server
sends out message to everyone on local network: “I need a DHCP server”
DHCP Offer: Find available IP addresses
DHCP server finds and selects an available IP address and sends it out to network: “Here is your IP address, DHCP client”
DHCP Request: DHCP client returns message of receipt
“Thanks for IP address, I will take it”
DHCP ACK: DHCP server acknowledges that IP is taken + issues DHCP lease which upon expiry, IP can be given to another device
To view specific DHCP steps:
DHCP Discover filter: dhcp.option.dhcp == 1
DHCP Offer filter: dhcp.option.dhcp == 2
DHCP Request filter: dhcp.option.dhcp == 3
DHCP ACK filter : dhcp.option.dhcp == 5
- Clarify that
dhcp.option.dhcp == 4is used for DHCP Decline. This is why DHCP ACK isdhcp.option.dhcp == 5.
DHCP Attacks
DHCP Starvation: a type of DDoS
- attacker accesses LAN, sends large volume of fraudulent DHCP messages over the network requesting IPs from server. If large enough, server may run out of IPs.
Mitigation of DHCP starvation:
- set a maximum threshold aka number of DHCP requests per second that can be accepted by server
DHCP Spoofing: AFTER starvation
- after DHCP Starvation attack, attacker can set up fraudulent DHCP server
- send out spoof messages to DHCP clients, identifying malicious router that clients should direct traffic to
- Once DHCP clients make this change, traffic is redirected
Mitigation of DHCP spoofing with DHCP Snooping:
- process implemented on a network switch that inspects packets to confirm they're legitimate DHCP offers + block the unauthorized
Routing Schemes and Protocols
Routing: The act of choosing the path that traffic takes in or across networks
Routing Schemes:
1. Unicast: Single device delivers a message to another single specific device, i.e. a phone call
2. Broadcast: Single device broadcasts to all devices on same network, i.e. DHCP broadcast, ARP broadcast
3. Multicast: Single device sends message to devices that have expressed interest in receiving message, i.e. subscription
Static Routing Vs Dynamic Routing
Static: manual configuration of a network route, usually by net admin
– smaller networks or less changes
– PRO: lower CPU on router, net admin has full control of their net's routing behaviour
– CON: fault tolerance; router can't be adjusted
Dynamic routing: network acts on its own to avoid network blockages
– network is adaptive
– primary routing techniques
– uses Routing Protocols
Dynamic Routing Protocols: 2 Primary Criteria
(1) Distance: amount of devices/hops used to get data from source to destination –> chooses least hops
– “Distance-Vector Routing Protocols” include:
-RIP: Routing Information Protocol: Uses hop count as main criteria
– EIGRP: Enhanced Interior Gateway Routing Protocol: Better than RIP because it only sends incremental updates, reducing workload on router and amount of data being transmitted
– More on comparison: https://community.fs.com/blog/eigrp-vs-ospf-differences.html
(2) Speed: Route is determined by time taken to move from source to destination
– just because a path has more hops does not make it slower
– “Link-State Routing Protocols include:
– OSPF: Open Shortest Path First:
Wireless Networking
- Wifi Standard: 802.11
WAP: Wireless Access Point: networking hardware device that connects a wireless network to a wired network by broadcasting a wireless signal called a beacon.
- must identify itself
- uses BSSID: Basic Service Set Identifier to identify its MAC address in a beacon signal in six hexadecimal octets
- also broadcasts SSID: Service Set Identifier using a more recognizable format that is easier to recognize for humans
- Wifi Security:
WPA2replacedWPAreplacedWEP
Wifi in Wireshark: Detect Security Protection Manually:
- click “Wireless” in toolbar + “WLAN Traffic”
- will show
SSIDs,BSSID, and wireless security protection If unable to detect security protection, the manual approach:
to add the different
SSIDsas a column:
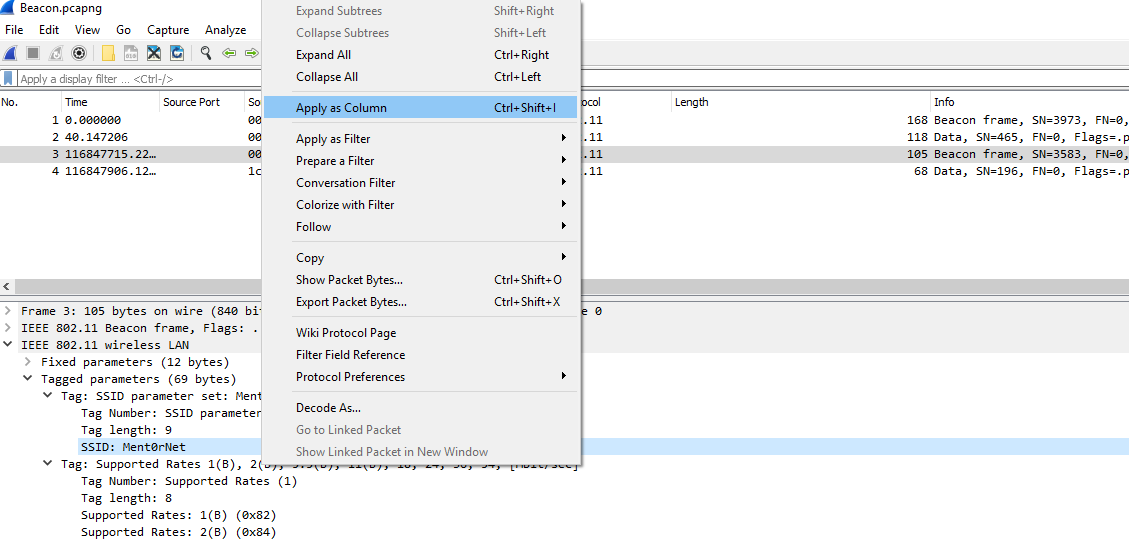 ]
]to add the security:
IEEE 802.11 wireless LAN>Tagged parameters>Tag: Vendor Specific: Microsoft Corp.: WPA Information ElementRight-click on
WPA Version: 1then selectApply as Column.
Decrypting with Aircrack-NG
- syntax is:
Aircrack-ng [.pcap file name] - Aircrack-NG needs a certain amount of wireless packets to figure out key, typically min 10k
- the Wireless Toolbar no longer exists in view > it is now in: Wireshark > Preferences > Protocols > IEEE 802.11
Wifi Security Vulnerabilities
Wardriving: driving/walking around with wireless-enabled device looking for unsecured wireless LANs
Warchalking: using chalk markings to show presence and vulnerabilities of wireless networks nearby
Warflying: Using drones
Evil Twin: Make a fake SSID to trick users to connecting to attacker's WAP